Case illustrates the “frequent gamble” one makes when posting on social media.
When you hear about Georgia, the name Duke, dealing with the cops, and the Confederate flag, you think Hazzard County, right? Or better yet, Daisy Duke. This case had a number of those elements, but presented a much more serious free speech question than Bo or Luke could have ever done.
 Plaintiff (named Duke), a captain at Georgia’s Clayton State University police department, posted a picture of the Confederate flag to his Facebook account with the caption “It’s time for the second revolution.” He was not on duty when he posted it, nor did he intend it to be visible by everyone (just friends and family). He claimed that he wanted to “express his general dissatisfaction with Washington politicians.” At the time, the police department had no social media policy that would have prevented the post.
Plaintiff (named Duke), a captain at Georgia’s Clayton State University police department, posted a picture of the Confederate flag to his Facebook account with the caption “It’s time for the second revolution.” He was not on duty when he posted it, nor did he intend it to be visible by everyone (just friends and family). He claimed that he wanted to “express his general dissatisfaction with Washington politicians.” At the time, the police department had no social media policy that would have prevented the post.
The chief of police demoted plaintiff and cut his pay by $15,000, stating that the Facebook post was inappropriate for someone in plaintiff’s position, and that officers should not espouse political views in public.
Plaintiff sued the police chief alleging, among other things, that his demotion over the Facebook post was a retaliation that violated his First Amendment rights. Defendant moved to dismiss. The court granted the motion.
It held that the police department’s legitimate interest in efficient public service outweighed plaintiff’s interest in speaking. The determination on this issue depended heavily on the content of the communication, and the fact that defendant was a police officer.
While the court acknowledged that plaintiff intended to express his disapproval of Washington politicians, it found that “on its face his speech could convey a drastically different message with different implications.” The court noted that order and favorable public perception were critical. “[A] police department is a ‘paramilitary organization, with a need to secure discipline, mutual respect, trust and particular efficiency among the ranks due to its status as a quasi-military entity different from other public employers.'” And police departments have a particular interest in maintaining “a favorable reputation with the public.” In sum, the court found, the speech at issue was capable of impeding the government’s ability to perform its duties efficiently.
The fact that the post was made off-duty and just to friends and family did not dissuade the court from finding the demotion to be proper. A local television station picked up the story that plaintiff had made the post. The court noted that “this illustrates the very gamble individuals take in posting content on the Internet and the frequent lack of control one has over its further dissemination.”
Duke v. Hamil, 2014 WL 414222 (N.D.Ga. February 4, 2014)

 Does an online service provider forfeit the safe harbor protections of the Digital Millennium Copyright Act if, when terminating the account of a repeat infringer, it does not delete all content the repeat infringer uploaded — infringing and noninfringing alike? A recent decision involving the antique internet technology Usenet sheds light on an answer.
Does an online service provider forfeit the safe harbor protections of the Digital Millennium Copyright Act if, when terminating the account of a repeat infringer, it does not delete all content the repeat infringer uploaded — infringing and noninfringing alike? A recent decision involving the antique internet technology Usenet sheds light on an answer.  Plaintiff sued a construction company and certain municipal authorities for negligence and loss of parental consortium after her toddler son was seriously injured in front of a construction site. Defendants sought broad discovery from plaintiff’s Facebook account, to which plaintiff objected in part. But the trial court required plaintiff to answer the discovery. So plaintiff sought review with the appellate court. On appeal, the court overturned the trial court.
Plaintiff sued a construction company and certain municipal authorities for negligence and loss of parental consortium after her toddler son was seriously injured in front of a construction site. Defendants sought broad discovery from plaintiff’s Facebook account, to which plaintiff objected in part. But the trial court required plaintiff to answer the discovery. So plaintiff sought review with the appellate court. On appeal, the court overturned the trial court. 
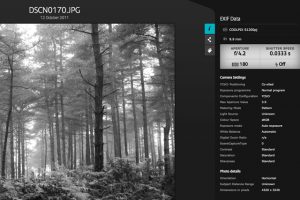 A digital photo’s
A digital photo’s 


 Defendant resigned from his job with an IT consulting firm. One of the firm’s customers hired defendant as an employee. Before the customer/new employer terminated the agreement with the IT consulting firm/former employer, defendant used the customer/new employer’s credentials to access and copy some scripts from the system. (Having the new employee and the scripts eliminated the need to have the consulting firm retained.) The firm/former employer sued under the
Defendant resigned from his job with an IT consulting firm. One of the firm’s customers hired defendant as an employee. Before the customer/new employer terminated the agreement with the IT consulting firm/former employer, defendant used the customer/new employer’s credentials to access and copy some scripts from the system. (Having the new employee and the scripts eliminated the need to have the consulting firm retained.) The firm/former employer sued under the  The Hollywood Reporter
The Hollywood Reporter